Managing SSL/TLS certificates for any web or mobile App platform is an essential part of the overall solution delivery these days. Ensuring that the communication within the App or across the network is encrypted and brings the necessary compliance into the overall product architecture is very much required for any enterprise be it in services or for a product-based company.
Now, With the increasing penetration of Containers and the rise of distributed architectures of products the requirements of having SSL certificates is now not limited to customer-facing applications.
The question is How do we solve the need of having SSL-based certificates when we deliver Serverless Applications or any services with Amazon Web Services(AWS). We are in this blog would be talking about the integration of SSL-based certificates into CloudFront distributions.
There are two ways CloudFront allows to manage the certificates of its distribution, either using Amazon Certificate Manager(ACM) or using custom SSL certificates. For Custom SSL certificates we would be evaluating Let’s Encrypt a Free SSL certificate initiative.
Managing Certificates with ACM(Amazon Certificate Manager)

- Goto CloudFront Distribution and under General click “Edit”.
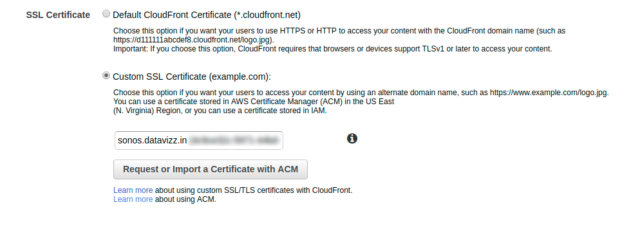
- Click on “Request of Import a certificate with ACM”
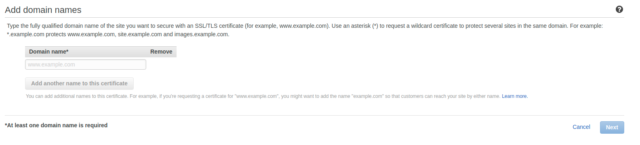
- Enter the Domain Name for which Certificate needs to be validated and Click Next.
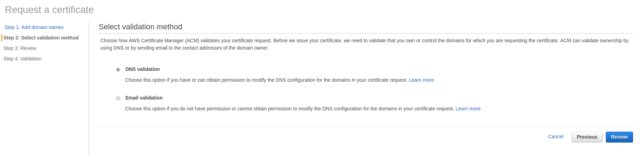
- Select the mode of Validation. You can validate the authority of that domain either by adding a DNS record or by Email Validation. In our case, we would be going ahead with DNS validation and click on Review.
- In the next step, you would be given the DNS record which needs to be added to your domain’s DNS. In case you are using Route53, it can be done automatically in ACM.
- Once the Certificate Status is in ISSUED mode. You can go back to CloudFront Distribution and update the Certificate under the ‘SSL Certificate’ section.
ACM is a free service and it doesn’t charge anything to manage the certificates. The charges would incur on the services like Cloudfront or ELB on which you would be deploying these certificates. One advantage of using ACM if you are using CloudFront is that you would be able to renew the certificates easily and at ease.
Managing Certificates with Let’s Encrypt

- Start the Ubuntu Docker image locally
- Install certbot using the following command
$ sudo apt-get update $ sudo apt-get install software-properties-common $ sudo add-apt-repository universe $ sudo add-apt-repository ppa:certbot/certbot $ sudo apt-get update $ sudo apt-get install certbot
- Create a new certificate
root@1e6e13dc47f3:/# certbot certonly --manual --preferred-challenges dns -d datavizz.in Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator manual, Installer None Obtaining a new certificate Performing the following challenges: dns-01 challenge for datavizz.in ------------------------------------------------------------------------------- NOTE: The IP of this machine will be publicly logged as having requested this certificate. If you're running certbot in manual mode on a machine that is not your server, please ensure you're okay with that. Are you OK with your IP being logged? ------------------------------------------------------------------------------- (Y)es/(N)o: y ------------------------------------------------------------------------------- Please deploy a DNS TXT record under the name _acme-challenge.datavizz.in with the following value: <<Some Code>> Before continuing, verify the record is deployed. ------------------------------------------------------------------------------- Press Enter to Continue Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/datavizz.in/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/datavizz.in/privkey.pem Your cert will expire on 2019-07-20. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
- Copy the generated certificates from docker image to local machine
$ root@1e6e13dc47f3:/# cd /etc/letsencrypt/live/datavizz.in/ $ root@1e6e13dc47f3:/etc/letsencrypt/live/datavizz.in# ls -l total 4 -rw-r--r-- 1 root root 543 Apr 21 10:46 README lrwxrwxrwx 1 root root 35 Apr 21 10:46 cert.pem -> ../../archive/datavizz.in/cert1.pem lrwxrwxrwx 1 root root 36 Apr 21 10:46 chain.pem -> ../../archive/datavizz.in/chain1.pem lrwxrwxrwx 1 root root 40 Apr 21 10:46 fullchain.pem -> ../../archive/datavizz.in/fullchain1.pem lrwxrwxrwx 1 root root 38 Apr 21 10:46 privkey.pem -> ../../archive/datavizz.in/privkey1.pem $ Ankitss-MacBook-Air:datavizz.in ankitsmacbook$ docker cp 1e6e13dc47f3:/etc/ letsencrypt/archive/datavizz.in/ . $ Ankitss-MacBook-Air:datavizz.in ankitsmacbook$ ls -l total 8 -rw-r--r-- 1 ankitsmacbook staff 543 Apr 21 16:16 README drwxr-xr-x 6 ankitsmacbook staff 192 Apr 21 16:16 datavizz.in $ Ankitss-MacBook-Air:datavizz.in ankitsmacbook$ cd datavizz.in/ $ Ankitss-MacBook-Air:datavizz.in ankitsmacbook$ ls cert1.pem chain1.pem fullchain1.pem privkey1.pem - Uploading certificate into IAM Certificate Store on AWS.
$ Ankitss-MacBook-Air:datavizz.in ankitsmacbook$ aws iam upload-server-certificate --server-certificate-name datavizz_in_April --certificate-body file://cert1.pem --private-key file://privkey1.pem --certificate-chain file://chain1.pem --path /cloudfront/<<CDNID>>/ --profile=DV { "ServerCertificateMetadata": { "ServerCertificateId": "<<SOME ID>>", "ServerCertificateName": "datavizz_in_April", "Expiration": "2019-07-20T09:46:51Z", "Path": "/cloudfront/<<CDNID>>/", "Arn": "<<ARN>>", "UploadDate": "2019-04-21T11:24:32Z" } } - Goto CloudFront and update the Certificate by removing the existing one and use the new certificate Name.
Let’s Encrypt is also a free service available to manage SSL certificates for your applications.
If you’re looking to see how Serverless Application design could make an impact in your organization, We are a Cloud-Native Application Development Company, we’d love to talk.