AWS Workspace is a managed, secure Desktop-as-a-Service(DAAS) service. During the ongoing situation across the globe everyone is moving towards Work From Home (WFH) in that case how do we ensure that we can secure the work environments for the developers that we have. We can start either Windows or Linux-based workloads.
Jeff Barr announced on 18th March a whole suite of services that can help people to leverage various services which would be available either free or in a limited capacity to ensure that work from home transition becomes easier for various industries.
Post that, I started exploring this AWS workspace service and understood various aspects of how can I get benefit from this service. Mainly there are a few interns in the office that needs a virtual workspace where they can access the necessary resources and ensure that we don’t have any data leakages in that.
One of the first things that I’d identified that natively AWS Workspaces doesn’t restrict users to copy and paste among their physical machines to the virtual workspace. Which is a very big security risk that could result in a data breach. So I had two quests in front of me:
How do I secure my Workspaces and how can I disable the clipboard in my Workspaces?
I’ve gone through various setups and finalized this architecture which would be easier to manage as well as low on the pocket. AWS Workspaces up to 50 devices is free till June but other services would incur costs to manage the workspaces centrally.
Here’s the architecture which I’d built.
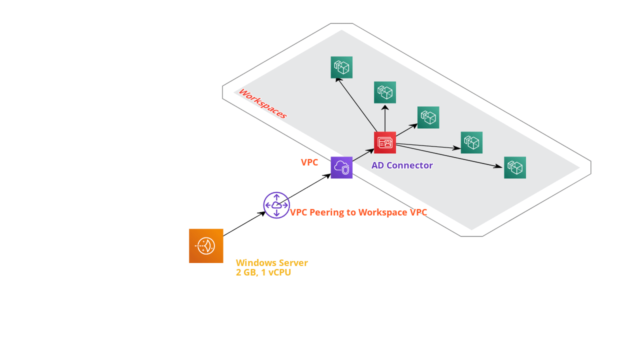
The following are the components that I’ve used in this architecture.
- AWS LightSail Instance – 2 GB, 1 vCPU – 20$/Month
- VPC Peering
- AD Connector (Directory Service) – Price is included in AWS Workspace cost (currently free – COVID-19)
- Windows Standard Workspaces (Currently Free – COVID-19)
Clipboard access restrictions are applicable through enforcing group policy objects which are not available for Linux based workloads.
Setting up Lightsail Instance
- Go to AWS Console and search for Lighsail from the product catalog and click on “Create Instance”
You can select a normal EC2 machine as well but Lightsail would be more cost-effective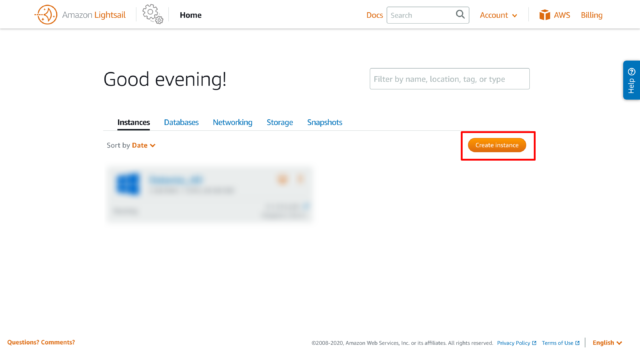
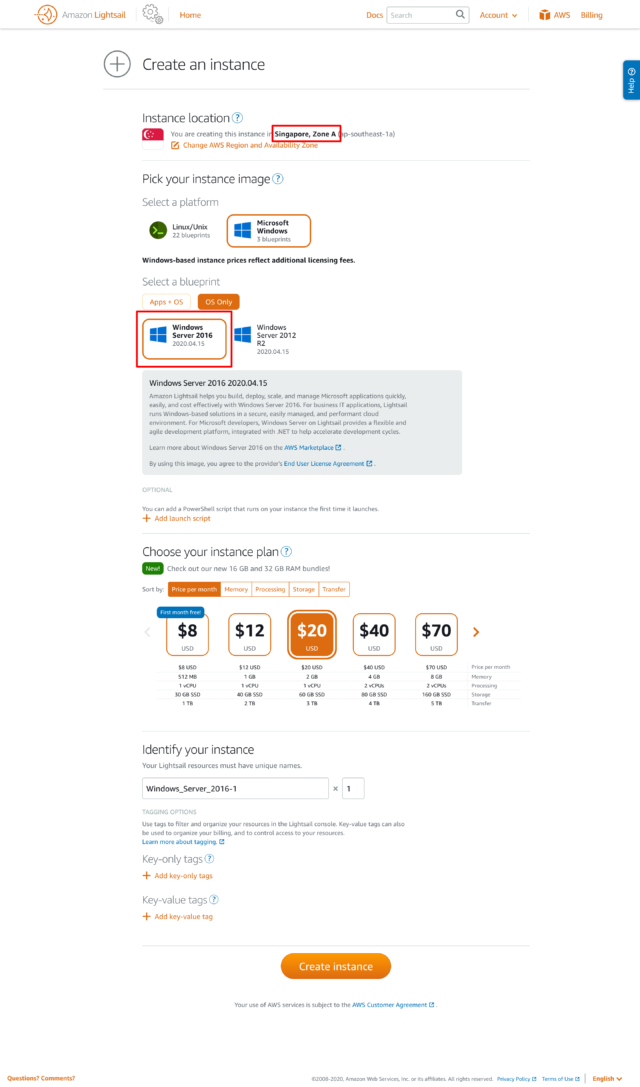
- Select the region the same as where you intend to deploy the workspaces. In my case, it was Singapore. Select the rest of the options and click on “Create Instance”.
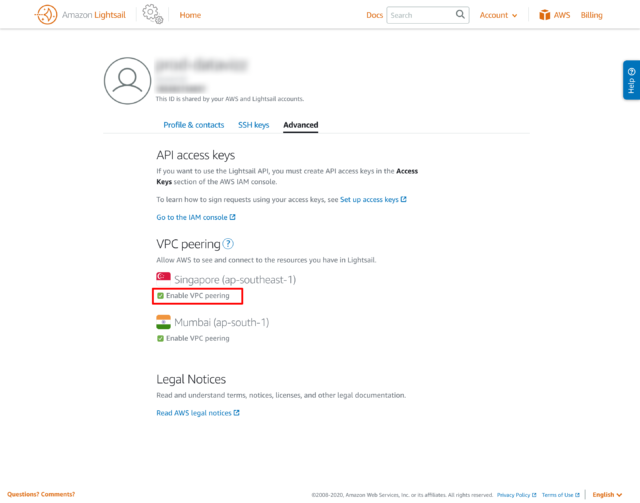
- Go to Account and then Advanced and click on Enabled VPC Peering against the region which you selected while creating the instance.
- Connect to the instance with the given credentials.
Setup Domain Controller
The next step is to install the required tools and services on the newly created instance through which we can provide necessary restrictions to our Workspaces.
- Open Server Manager from the Start screen by choosing Server Manager.
- In the Server Manager Dashboard, choose Add roles and features,
- In the Add Roles and Features Wizard choose Installation Type, select Role-based or feature-based installation, and choose Next.
- Under Server Selection, make sure the local server is selected, and choose Features in the left navigation pane.
- In the Features tree, open Remote Server Administration Tools, Role Administration Tools, select AD DS and AD LDS Tools, scroll down and select DNS Server Tools, and then choose Next.
- Review the information and choose Install. When the feature installation is finished, the Active Directory tools are available on the Start screen in the Administrative Tools folder.
- Click on “Promote this machine to be domain controller” and then create your domain-like corp.datavizz.in in my case.
- Go to Active Directory Users and Computer now to create a new Organizational Unit to limit certain workspaces to have restrictions that we needed.
- Then click on a new User which we would be used as an account which would be used to authenticate AD Connector.
Install Group Policy Administrative Template
Now we would be installing the required Administrative template on our Domain controller(Lightsail instance) to enforce required policies from instance to Workspaces.
- From a running Windows WorkSpace, make a copy of the pcoip.adm file in the C:Program
Files (x86)TeradiciPCoIP Agentconfiguration directory. - Open the Group Policy Management tool (gpmc.msc) and navigate to the organizational unit in your domain that contains your WorkSpaces machine accounts.
- Open the context (right-click) menu for the machine account organizational unit and choose to Create a GPO in this domain, and link it here.
- In the New GPO dialog box, enter a descriptive name for the GPO, such as WorkSpaces Machine Policies, and leave Source Starter GPO set to (none). Choose OK.
- Open the context (right-click) menu for the new GPO and choose Edit.
- In the Group Policy Management Editor, choose Computer Configuration, Policies, and
Administrative Templates. Choose Action, Add/Remove Templates from the main menu. - In the Add/Remove Templates dialog box, choose Add, select the pcoip.adm file copied previously, and then choose Open, Close.
- Close the Group Policy Management Editor. You can now use this GPO to modify the Group Policy settings that are specific to Amazon WorkSpaces.
Configure AD Connector to connect with our new AD
We would now go to the AWS console and select directory service from the product selection bar.
- Click on “Setup Directory”
- Select “AD Connector” and click “Next”
- Select Directory size based on your requirements
- Select VPC as required
- Directory DNS Name – (Same as Forest name which you provided earlier)
- DNS IP address – Private IP of Lightsail Account
- Username and Password – Which you created during AD Setup
The status should be “Active” if all the configurations are good.
Setup Workspace
Go to the workspace and create a new workspace using the directory same as what we configured as AD Connector and then validate if the clipboard access is disabled or not!
We at DataVizz are AWS Consulting Partners and been helping organizations in adapting to the cloud easily and effectively. Do reach out to us in case of any further questions or any feedback on this article.
Don’t forget to leave down your review and do give me your comments on what you would like to see next!


